Yearly coverage for the cost of a single Pentest!
Attackers scan your network every day, so why don’t you? With PTaaS from Xcape, Inc.® we stagger our automated vulnerability scans and attacks providing our customers with better visibility into tomorrow's issues today with real-time reporting from an easy to use dashboard.
Why scan for vulnerabilities quarterly when you can get daily visibility into what vulnerabilities your organization is put at risk by with our PTaaS automated vulnerability scanning and attack platform. Schedule a demo to see why ours is different. Or take a look for yourself!
What is PTaaS?
Penetration Testing as a Service (PTaaS) combines over 50 automated vulnerability scanning tools, open source intelligence scanning, and automatic attacking of vulnerable infrastructure into a tool for our pentesters to use for finding validation, privilege escalation, and exploit development. With PTaaS, our pen testers spend more time hacking your infrastructure because all the easily repeatable tasks of scanning and attacking vulnerable end-points are done for us by our Xcape Blended Methodology Adversary Simulation (XBMASXcape Blended methodology adversary simulation is a security testing method that combines various techniques to identify vulnerabilities in a system or application by simulating the actions of a malicious actor. It is used to assess the security of complex or high-risk systems.) engine.
Watch the video below to learn more about our PTaaS solution, or keep scrolling to learn more and get signed up!
How does Pen Testing as a Service work?
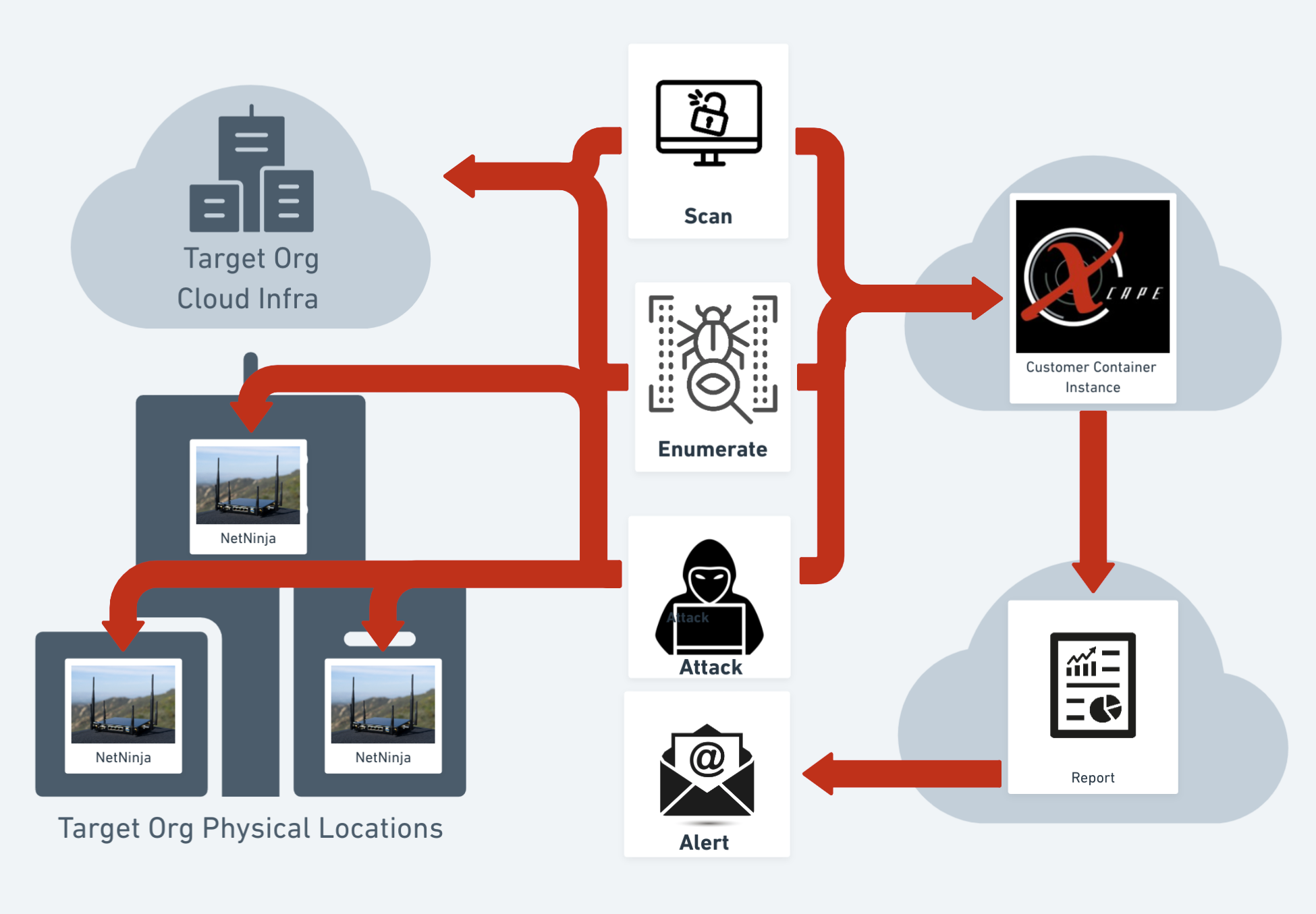
Scan
By leveraging automation for scanning, it allows our team at Xcape to complete the most arduous tasks of the beginning of most pen tests; access to our clients target environment, asset enumeration, vulnerability scanning, and exploiting vulnerable targets.
Scanning open source intelligence (OSINT) sources for evidence of compromised accounts, leaked passwords or other private information related to the business, its owners, and key staff.
At this stage we know a lot about your business, its technical footprint, and what data about its stakeholders that's been made public, all of this data is used for enumeration.
Enumerate
Our automated enumeration engine provides a great baseline of your organizations risk exposure based on the systems and services that are in use to satisfy your organizations technical needs.
At this stage our engine is scanning assets that were identified in your external and internal* infrastructure scan for vulnerabilities that it might be able to exploit, every known exploitable system is then cataloged in our system for later use.
Attack
The last part of a true penetration test is using vulnerable targets to gain access to an otherwise secure system to identify intellectual property or proprietary information that might be at risk during an attack.
With the scanning and vulnerability and asset enumeration data, our automated system will systematically attack the vulnerable parts of your infrastructure, so that one of our pentesters can spend more of their time working on exploit development, and attack methodologies simulating the work any attacker would do for a system they deemed interesting.
Because of the difficulty in automating kill chain attacks humans do the last 30% of our automated workflow to both qualify findings and launch privilege escalation attacks on systems PTaaS already gained access to through automation.
Report
Then automated reports are generated monthly with findings enriched from over 50 data sources, verified by our team of senior penetration testers with additional screenshots and code execution from their efforts. All compiled into a nice easy to digest report.
With visibility into internal and external infrastructure we're not only protecting the external facing infrastructure, but we're addressing what happens when an attacker makes it past the perimeter, working with our clients to build an IR and Ops plan to keep their business resilient even while mitigating a breach.
Alert
Our system automatically flags humans (our team and yours) when a critical or high finding is identified in the system, we review the findings to determine their viability and business impact updating your report with remediation advice.
Our PTaaS Techniques
#NotAnotherScanner Our PTaaS offering isn't just another scanner, our automated attack platform is constantly evolving and part of our standard pentesting methodology.
Red Team Abilities |
Blue Team Abilities |
|---|---|
Blended Threat AssessmentsA blended threat assessment combines multiple techniques to identify and assess vulnerabilities and risks to an organization. It is used to identify potential threats and develop a plan for addressing them. |
Incident ResponseIncident response is the process of identifying, responding to, and resolving incidents within an organization. It helps minimize the impact of incidents and restore normal operations. |
OSINTOSINT (Open Source Intelligence) is the process of collecting, analyzing, and disseminating information from publicly available sources. It is often used by organizations to gather intelligence on potential threats, targets, or subjects of interest. OSINT can include a variety of sources, such as social media, news articles, blogs, and public databases. Discovery |
Ransomware RecoveryRansomware attack recovery involves taking steps to restore systems and data after a ransomware attack. It may include identifying and isolating infected systems, restoring data from backups, and implementing measures to prevent future attacks. |
Vulnerability AssessmentsA vulnerability assessment is a process for identifying and quantifying vulnerabilities in a system or network. It helps organizations prioritize and address potential vulnerabilities. |
Threat HuntingThreat hunting is the proactive search for potential threats within an organization's networks, systems, and data. It is performed by cybersecurity professionals to identify and disrupt potential threats before they can cause harm. |
Penetration TestingPenetration testing is a simulated cyber attack on a computer system, network, or web application to test its defenses and identify vulnerabilities that an attacker could exploit. |
IR Program Development ConsultingAn IR (Incident Response) program is a formalized process for identifying, responding to, and resolving incidents within an organization. |
Staggered Attack Surface EnumerationStaggered attack surface enumeration is a security testing technique that identifies and analyzes access points within a system or network in a phased manner. |
Customized Solution DevelopmentBlue team solution development involves creating security solutions tailored to an organization's specific needs and requirements. It includes assessment, design, implementation, and ongoing maintenance to ensure effectiveness in protecting systems and data. |
Automated Adversary EmulationAutomated adversary emulation is the use of tools and techniques to simulate the actions and behaviors of cyber adversaries in order to test an organization's defenses and identify vulnerabilities. |
Adversary EngagementAdversary engagement is the process of actively interacting with and attempting to disrupt or neutralize potential threats or adversaries. |
How about a Demo?
Schedule a Demo
Click the button below to schedule a demo with our team, to take a closer look at what our PTaaS from Xcape, Inc.® has to offer.
What does PTaaS Cost?
| Packages | Start-Up | Basic | Standard | Professional | Enterprise |
|---|---|---|---|---|---|
| Host | 5 | 50 | 100 | 200 | Call Us |
| Internal / External | External | External | Both | Both | Both |
| Addtl Host | $50 Each | $50 Each | $75 Each | $100 Each | Call Us |
| Price | $625 / mo | $2.5k / mo | $5k / mo | $10k / mo | Call Us |
PTaaS Package Details
| Features | Start-Up | Basic | Standard | Professional | Enterprise |
|---|---|---|---|---|---|
| XBMAS Appliance Included * | ✕ | ✕ | ✓ / 1 | ✓ / 2 | Call Us |
| *Appliances are required to scan each target locations internal network. Additional units are $800 each | |||||
| OSINT Discovery | ☐ | ☐ | ☐ | ☐ | ☐ |
| On-Going Attack Surface Enumeration | ☐* | ☐* | 🗹 | 🗹 | 🗹 |
| On-Going Staggered Penetration Testing | ☐* | ☐* | 🗹 | 🗹 | 🗹 |
| Integrated Post Exploitation | ☐* | ☐* | 🗹 | 🗹 | 🗹 |
| Findings Manual Review Addtl @ $299 / hr |
☐ 2 Hrs | ☐ 4 Hrs | 🗹 8 Hrs | 🗹 16 Hrs | Call Us |
| Scheduled Manual Post Exploitation Addtl @ $399 / hr |
✓ 1 Hr | ✓ 2 Hrs | ✓ 4 Hrs | ✓ 8 Hrs | Call Us |
| Scheduled Threat Hunting and Response Addtl @ $299 / hr |
✕ | ✕ | ✓ 2 Hrs | ✓ 8 Hrs | Call Us |
| Incident Response Addtl @ $399 / hr |
✕ | ✓ 1 Hrs | ✓ 2 Hrs | ✓ 3 Hrs | Call Us |
PTaaS Add-On's
Email Phishing Campaigns by IRONSCALES
Email Phishing Campaigns
Utilizing IRONSCALES platform we provide e-mail Phishing Simulation and Training, Account Takeover protection and remediation, as an add-on for PTaaS customers.
Get seamless API Integration with Microsoft O365 & Google Workspace. This email security service is designed to come to you and scale with your business. Using native API integrations, you can deploy in minutes with no configuration changes, risks, or interruptions.
| Package | Features | Pricing |
|---|---|---|
| Core | Core is a new bundle of advanced email security services and training, including AI powered incident response, mailbox-level business email compromise (BEC), crowdsourced real time threat protection, phishing simulation and training, and a Virtual SOC analyst. | $3.25 / Mailbox |
| Core Plus | Core Plus includes the full range of email security, anti-phishing, and security training products. | $6.00 / Mailbox |
| Complete Protect | Complete Protect delivers the most comprehensive protection with the addition of Account Takeover (ATO) protection and advanced messaging security for Microsoft Teams to the Core Plus plan. Complete Protect combines automated anti-phishing technologies with Security Awareness Training into a seamless and tightly integrated single solution. | $8.33 / Mailbox |
Social Engineering Campaigns
Social Engineering
We provide social engineering services as an add-on providing another dimension to on-going testing.
XBMAS Appliance
 Our NetNinja is the core of our Xcape Blended Methodology Adversary Simulation platform that provides our testers a platform for launching attacks against our customers internal wired, and wireless infrastructure, providing not only great external risk visibility, but also providing our customers the ability to understand how an attacker would pivot though their environment in the event of an attack, so we can work with them to mitigate an attackers access post breach.
Our NetNinja is the core of our Xcape Blended Methodology Adversary Simulation platform that provides our testers a platform for launching attacks against our customers internal wired, and wireless infrastructure, providing not only great external risk visibility, but also providing our customers the ability to understand how an attacker would pivot though their environment in the event of an attack, so we can work with them to mitigate an attackers access post breach.
What's the process to get started?
Use the below on-boarding form to get started, or Schedule a Free Consultation with the button below.
On-Boarding Questionnaire
The toggle switch above the submit button will send you a copy of your responses.
FAQ
How does our Pen Test as a Service compare?
We've automated the most time consuming, and important part of pentesting, scanning, host enumeration, and most importantly initial access. With all the time saved with the automation of reconnaissance and exploitation activities that gives our pentesting team the ability to focus on post exploitation activities and attack vectors.
We've done the work for you comparing our Penetration Testing as a Service offering with other competitors to highlight the main difference in what we call PTaaS versus everyone else's definition, we were limited in terms of what we had access to in terms of public information. Click below to see the side by side comparison on how we stack up against the competition.
How does Reporting work?
The reporting is automated and at any time you can login to the reporting dashboard to review findings from our scans. We provide 1 report a month that deduplicates findings so that we focus on new risks as they are exposed by our system.
How does Xcape, Inc.® responds to incidents?
Our standard Service Level Agreement with our PTaaS customers is 1 hour for all vulnerabilities identified as critical, and 3 hours for items marked High.
How soon can we start a pentest using the Xcape, Inc.® PTaaS platform?
Once all your host are listed the PTaaS engine the results of your first scan will populate in our dashboard within the next 24 hours.
What are the tactics and tools used by PTaaS?
Tactics used by PTaaS
We've blended OSINT tools and tactics from the MITRE ATT&CK framework along with some tricks from our own tools, to simulate what an attacker might do.
Tools Used by PTaaS
- AbstractAPI
- AbuseIPDB
- Abusix Mail Intelligence
- AlienVault
- BinaryEdge.io
- BitcoinAbuse
- Botscout.com
- Builtwith.com
- Censys.io
- CertSpotter
- CIRCL.LU
- EmailCrawlr
- Etherscan.io
- Focsec
- Fraudguard.io
- FullHunt
- Grayhat Warfare
- GreyNoise
- HaveIBeenPwned
- Hunter.io
- Hybrid Analysis
- IntelligenceX
- IBM X-Force
- Ipapi.com
- Ipinfo.io
- IPQualityScore
- Ipregistry
- Ipstack.com
- JsonWHOIS.com
- Koodous
- Leak-Lookup
- LeakIX
- Malwarepatrol.com
- MetaDefender
- NameAPI
- Nessus
- NetworksDB
- NeutrinoAPI
- Numverify
- Onyphe
- PasteBin search
- Projecthoneypot.org
- Pulsedive
- RiskIQ
- RunZero
- Security Trails
- seon.io
- SHODAN
- Snov.io
- Social Media Profiles
- TextMagic
- Twilio
- ViewDNS
- VirusTotal
- WhatCMS
- Whoxy.com
- Wigle.net
- ZoneFiles.io
- XBMAS
- Xcape, Inc.®: Internal Exploit Tools
- And More!
What defines a "host" for PTaaS scans?
Host are defined as any "target" that the system is pointed at. Below are the different types of host we support scanning:
- ASN’s
- BitCoin Wallets
- Cloud Infrastructure
- Domain Names
- Emails
- Human Names
- Internal Infrastructure
- IP’s
- Phone Numbers
- Servers
- Subnets
- User Names
- Workstations
What frequency are PTaaS scans run at?
Our vulnerability scan and host enumeration engine run for multiple hours, and the start times are staggered randomly throughout the day over the course of every 31 day scan period simulating real world adversarial conditions and testing your infrastructure at different times throughout the day.
